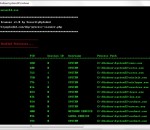
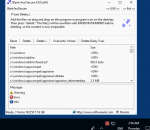
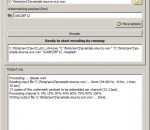
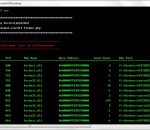
Command-line Tool to Scan and Show DEP enabled Processes
Delete your sensitive files permanently. Mutilate File Wiper is a file remover that prevents recovery of deleted files from your hard drive by data recovery or forensic software. Choose one of three security levels or configure a customizable level for up to 297 overwrites. Mutilate supports complete folder and subfolder shredding. With Mutilate's disk free space wiper, you can even use Mutilate to permanently erase previously deleted files.
Dashlane is a comprehensive e-commerce manager that can help you save time when dealing with your multiple Internet accounts. It is always advisable to keep your usernames and passwords in a secure place, so that no one else can access and use them. Dashlane is an intuitive and powerful application that can help you do that.
Touch N Go is a Biometric Framework (SDK or API) that allows programmers to integrate fingerprint recognition in their application with just FOUR lines of code. It supports multiple database (Oracle, MS SQL, MySQL Enterprise, Sybase, and IBM DB2, etc.) and multiple programming languages (C/C++, C#, .NET, VB.NET, F#.NET, Java, Ruby, Delphi, etc.). It also supports most fingerprint scanners available in the market.
"Blank And Secure" is a portable tool to securely delete the data. Secure delete files are required to block the recovering of deleted data. Secure deletion is possible with this program, because "Blank And Secure" overwrites the data with zeros before deleting. The data recovery is impossible after this operation. So please only use if the data really should be permanently deleted.
Protect your data against illegal access with the abylon CRYPTDRIVE. The encrypted drives can be open with passwords, chip cards, removable media (e.g. memory stick), CD or X.509-certificate. Only with correct authentication the CRYPTDRIVE is displayed in the File Explorer as drive and the access to the encrypted data is possible. If you lose your notebook, the closed drives are invisible and secure like a safe through AES or Blowfish encryption.
Audio Watermarking Tools 2 (AWT2) of www.audiowatermarking.info are software utilities for embedding (and extracting) short data payload within audio streams (wave files). The tools are distributed as a package of GUI and console utilities running on Microsoft Windows, Apple Mac OS X and Linux. The watermark is highly robust. It survives almost all kinds of audio conversions: transcoding using MP3, Ogg Vorbis, air transducing, etc.
The Terminator system - to be more exact HSS (hardware-software system). Terminator consists of an external hardware controller (Terminator controller controller itself) pluggable into an USB port of a computer and the free Terminator program. The Terminator system was made by the best IT specialists of our organization. It combines the newest engineering solutions, ultimate control compliance, compactness and simplicity.
Identity Protector Secures your Identity and Passwords so that you can think about the more important things in life.Identity Protector scans your computer for any traces of Personal Information and any saved passwords and locks them away in a Vault on your system that can only be accessed by a single Master Key password that you create. Even we don't know your password because it's encrypted on our servers.
PWGen is a password generator capable of creating large amounts of cryptographically-secure passwords or passphrases (from word lists). It uses a random pool to gather entropy from user inputs and system parameters. Offers text encryption and random data file creation, too.
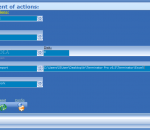
Command-line Tool to Find the DLL in all Running Processes