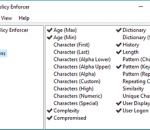
Windows has a basic password complexity rule, but it accepts many weak passwords like "Secret1" and "Pa$$word". Password Policy Enforcer's configurable rules allow you to enforce almost any password policy imaginable. You can even create multiple password policies and assign them to individual users, groups, and Organizational Units.
Real-time protection against online threats such as hacked or infected web pages. Makes your Internet experience safer. * Protects you before you visit a poisoned web page * Clear safety ratings for search results in Google, MSN and Yahoo * Compatible with most popular antivirus and security suite products * Analyzes pages, not sites, so you’re not blocked from a whole site if one page is poisoned
The Password Gorilla helps you manage your logins. It stores all your user names and passwords, along with login information and other notes, in a securely encrypted file. A single “master password†is used to protect the file. This way, you only need to remember the single master password, instead of the many logins that you use.
HashPass is a password generator that revolutionizes the way you use your passwords. Based on your individual and safely entered criteria, it mathematically transfers your password-to-be into a unique secure hash with length of up to 128 characters which becomes your real password and which can be next pasted manually or automatically into any text-input-capable target or dragged into drag-and-drop enabled destinations (password edit boxes).
BestCrypt is easy-to-use, powerful data encryption software. You allocate a portion (container) of free space of your drive where you keep all your sensitive data in encrypted form. BestCrypt creates a virtual drive in your system which you work with like with any other drive. All data written there are encrypted "on-the-fly". Strong encryption algorithms Rijndael (AES), Blowfish,Twofish, GOST, DES. Time-out and Hot Key options.
FayeTRACKER is a replacement application for the netstat feature in Windows. It offers the same functionality as the netstat command, but has many more features and it makes it much easier to see how applications are connected to the Internet. The software doesn't need installing and running the program's executable is all that takes.
Passwords and other information can be transferred to other applications automatically. You will have fewer login problems. You'll never have to worry about forgetting a password or losing access to critical applications or web sites. All you need to remember is one master password.
The DeEgger Embedder is a piece of privacy software for Windows. It's designed to allow the user to create files that have other files hidden inside them. It takes a file of any kind, and merges it's binary (1s and 0s) with the binary of any media file (.avi, .jpg, .mp3, .mp4, .pdf, .png). The new media file presents as it normally would, however your secret file is woven into it's binary and can be extracted using this software.
The file-safe automatically encrypts all files in the CRYPT-folder without entering the password every time. The the one-time entry of the password is sufficient to access the saved files and unauthorized users can not open this. Changes in the files will be updateded in the encrypted files automatically and the file-based design enables simultaneous access to multiple authorized users.
The InfoLock application is designed so that it can provide ultra secure encryption of valuable information and documents. The software uses a unique algorithm that combines a passphrase and an optimized passkey to produce a very long, unintelligible master key with which to encode the information.
Program can hash data from keyboard, file or CD/DVD by Adler32, CRC32, CRC64, GOST, HAVAL, MD2, MD4, MD5, MD6, SHA-0, SHA-1, SHA-1-IME, SHA-224, SHA-256, SHA-384, SHA-512, RIPEMD-128, RIPEMD-160, RIPEMD-256, RIPEMD-320, TIGER or Whirlpool algorithm.